B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ ensures that authorized users have timely and reliable access to necessary information.
A) Availability
B) Integrity
C) Confidentiality
D) Concealability
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Perfective maintenance _____.
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) competes for resources in an operational system
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ protects information from unauthorized disclosure and safeguards privacy.
A) Availability
B) Integrity
C) Confidentiality
D) Accessibility
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Matching Identify the letters of the choices that best match the phrases or definitions. -Hostile act that targets systems or a company itself
A) Private key encryption
B) Public key encryption
C) Network interface
D) Asset
E) Mitigation
F) Transference
G) Attack
H) Security
I) Keystroke logger
J) Software reengineering
L) D) and J)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Matching Identify the letters of the choices that best match the phrases or definitions. -Records everything that is typed into the keyboard, including passwords, while the system continues to function normally
A) Private key encryption
B) Public key encryption
C) Network interface
D) Asset
E) Mitigation
F) Transference
G) Attack
H) Security
I) Keystroke logger
J) Software reengineering
L) A) and E)
Correct Answer

verified
Correct Answer
verified
True/False
The hardening process that makes a system more secure is fully automatic.
B) False
Correct Answer

verified
Correct Answer
verified
True/False
In a broad sense, credentials include formal degrees, diplomas, or certificates granted by learning institutions to show that a certain level of education has been achieved.
B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The _____ is the configuration of a system documented at the beginning of the project and consists of all necessary system requirements and design constraints.
A) functional baseline
B) extension baseline
C) allocated baseline
D) product baseline
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ include changing programs, procedures, or documentation to ensure correct system performance; adapting the system to changing requirements; and making the system operate more efficiently.
A) Team building activities
B) Elicitation activities
C) Maintenance activities
D) Testing activities
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A help desk can boost its productivity by using _____, which allows IT staff to take over a user's workstation and provide support and troubleshooting.
A) high-level synthesis
B) wireless fidelity
C) word editing software
D) remote control software
F) None of the above
Correct Answer

verified
Correct Answer
verified
True/False
In a public key encryption environment, each user on the network has a pair of keys: a foreign key and a private key.
B) False
Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ is a process for controlling changes in system requirements during software development.
A) Data management
B) Disk management
C) Configuration management
D) Email management
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Matching Identify the letters of the choices that best match the phrases or definitions. -Uses analytical techniques to identify potential quality and performance improvements in an information system
A) Private key encryption
B) Public key encryption
C) Network interface
D) Asset
E) Mitigation
F) Transference
G) Attack
H) Security
I) Keystroke logger
J) Software reengineering
L) D) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ develops safeguards that reduce risks and their impact.
A) Risk assessment
B) Risk verification
C) Risk identification
D) Risk control
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ prevents unauthorized users from creating, modifying, or deleting information.
A) Availability
B) Integrity
C) Confidentiality
D) Evacuation
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Typically, an intruder accesses a system using a compromised account, and may attempt a(n) _____, which is an unauthorized attempt to increase permission levels.
A) privilege escalation attack
B) denial-of-service attack
C) malware penetration attack
D) identity management invasion
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
To avoid problems, preventive maintenance _____.
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) requires analysis of areas where trouble is likely to occur
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A(n) _____ is a centralized resource staffed by IT professionals who provide users with the support they need to do their jobs.
A) help desk
B) white spot
C) maintenance software module
D) utility point
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
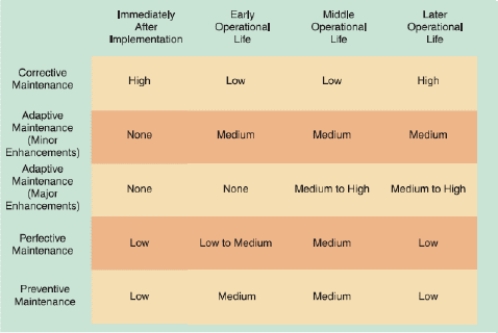 -As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor _____ maintenance.
-As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor _____ maintenance.
A) corrective
B) adaptive
C) perfective
D) preventive
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 81
Related Exams